This guide walks you through the steps for creating an IAM role for authenticating RudderStack while setting up the following destinations:
Cloud destinations
Warehouse destinations
- Amazon Redshift
- Amazon S3 Data Lake
- Azure Synapse
- ClickHouse
- Databricks Delta Lake
- Microsoft SQL Server
- PostgreSQL
- Snowflake
Creating a RudderStack IAM role
To set up a new RudderStack IAM role, follow these steps:
- Sign in to your AWS Management Console and open the IAM console.
- In the left navigation pane, click Roles followed by Create role.
- Under Trusted entity type, select AWS account, as shown:
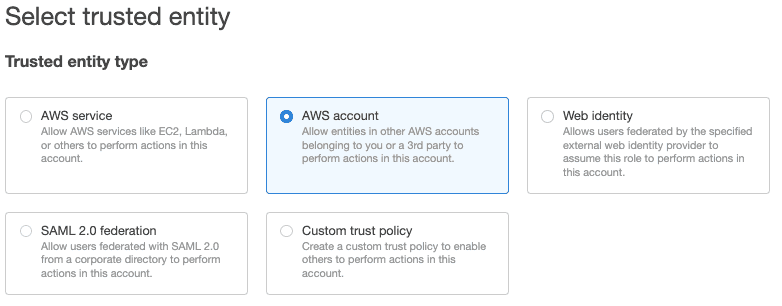
- Select Another AWS account and under Account ID, enter
422074288268, the account ID associated with RudderStack. - Under Options check Require external ID and enter your workspace ID as the External ID.
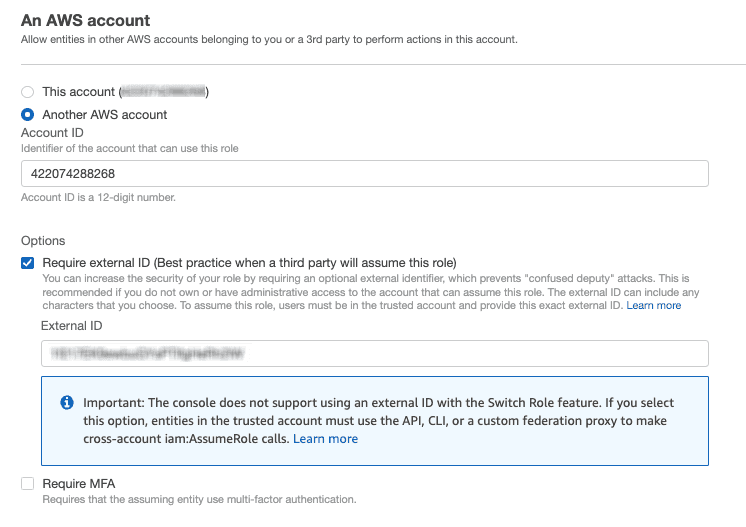
- Review all the settings carefully and click Next to proceed.
- Select your destination-specific permission policies applicable for the RudderStack IAM role. To create a new policy from scratch, click Create policy. For more information, refer to the Creating IAM policies guide.
- Optional: You can also set a permissions boundary. Expand the Set permissions boundary section, choose Use a permissions boundary to control the maximum role permissions, and select the policy to use for the permissions boundary. An example is shown below:
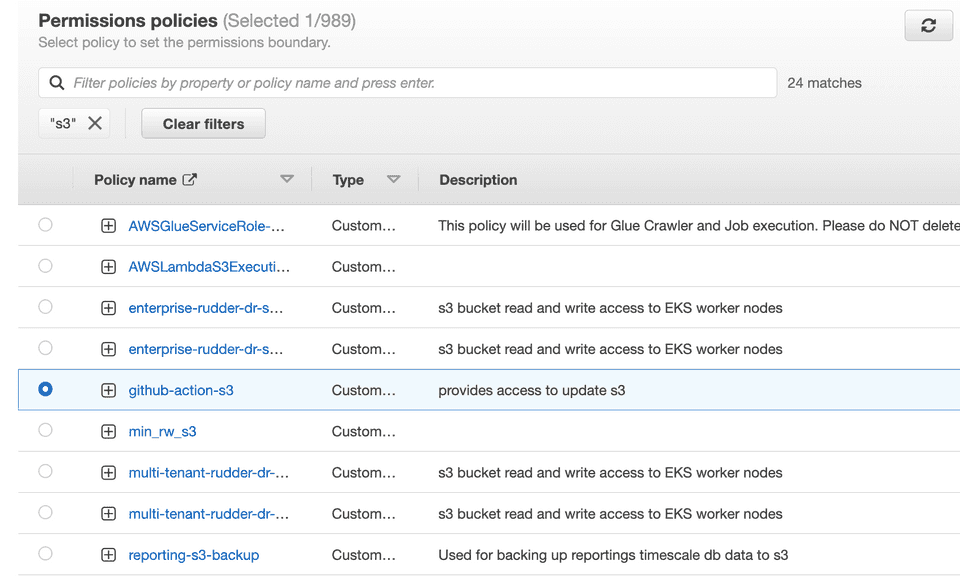
- Review all the settings carefully and click Next to proceed.
- Enter a unique name for your role. Note that this name cannot be distinguished by case. For example, you cannot create a role named
RUDDERSTACKifrudderstackalready exists.
- Optional: Enter the description for this role.
- To edit the use case or permissions for the role, click the Edit button next to the Step 1: Select trusted entities or Step 2: Add permissions, respectively.
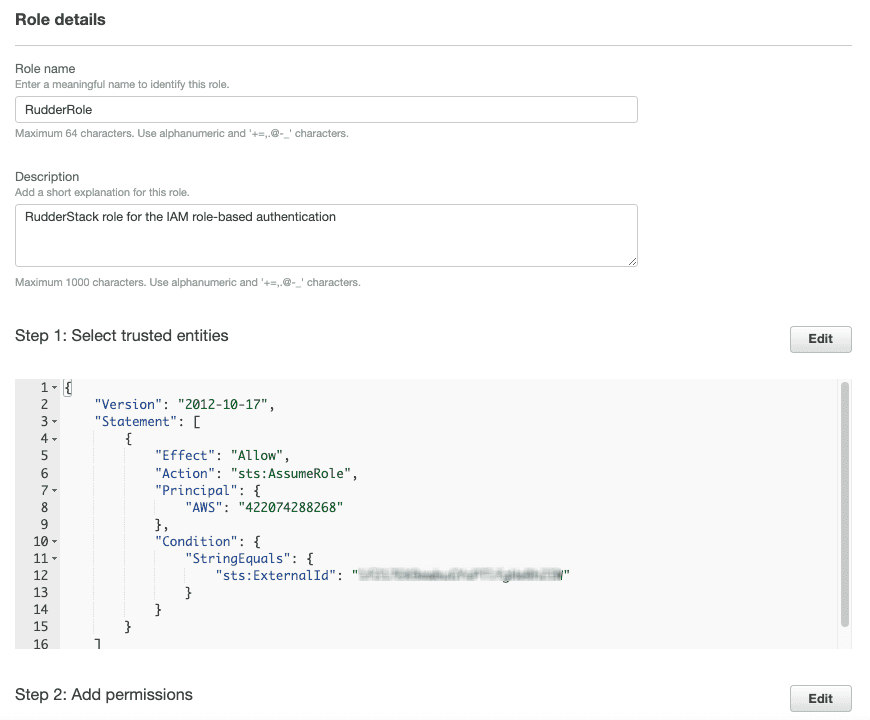
- Optional: You can also add metadata to the role by attaching tags as key-value pairs. For more information, refer to the Tagging IAM resources guide.
- Click Create role to complete the setup.
- Finally, note the ARN of this newly created role.
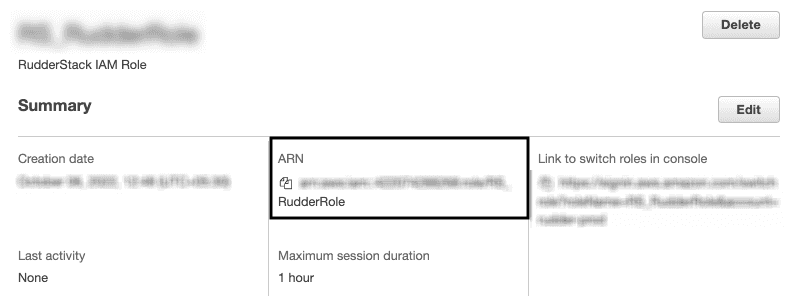
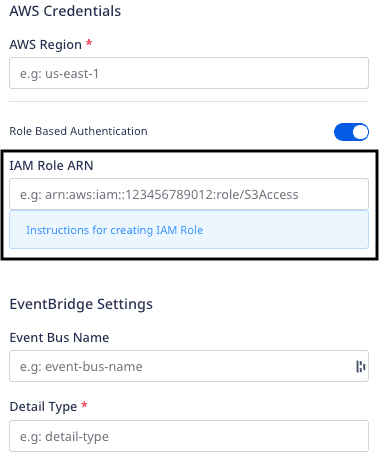
This ARN is required while configuring your AWS destination when you enable the Role-based Authentication setting, as shown:
Destination-specific policy permissions
Refer to the following sections for the destination-specific policy permissions:
Contact us
For more information on the topics covered on this page, email us or start a conversation in our Slack community.